






















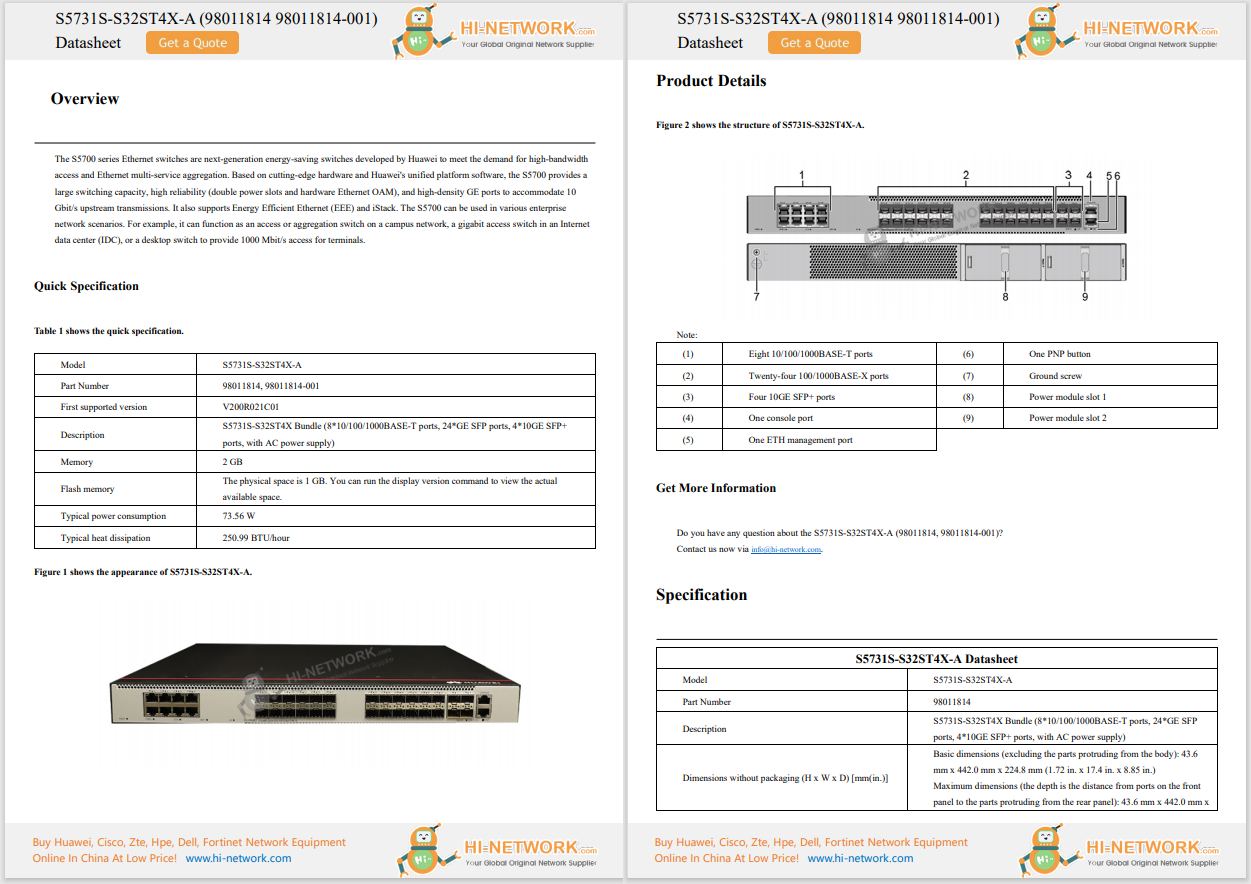




When your policies live in silos, your security does too.
I talk to a lot of security leaders who think they've "modernized" because they've got secure web gateway (SWG) from one vendor, cloud access security broker (CASB) from another, and zero trust network access (ZTNA) from a third. On paper, it looks like a strong stack. In practice, it's a maze of consoles, redundant rules, and gaps where policies simply don't follow the user.
In a fast-moving environment, that's more than a nuisance; it's a liability. One missed update, one misaligned rule set, and your "secure" architecture turns into an open door. If your security service edge (SSE) platform can't enforce consistent policies everywhere, it's not protecting you the way you think it is.
Not long ago, "best of breed" was the go-to strategy. Organizations built capabilities like SWG, CASB, and ZTNA from different vendors, layering in domain name service (DNS) security, firewall services, and more.
Individually, those tools worked. Together, they created a patchwork that requires constant integration work, duplicate policies, and never-ending troubleshooting. Many can't even share a common identity model or threat context.
The results?
Cisco Secure Access changes that.
It unifies SWG, CASB, ZTNA, DNS-layer security, and firewall services under a single cloud-native policy engine. Whether a user connects to a sanctioned SaaS app from a managed laptop or a sensitive internal system from a bring your own device (BYOD) phone, the same policy follows-automatically and in real time.
This isn't a stitched-together dashboard. It's a unified architecture with:
The result: policy enforcement that moves with the user, not just the network.
From customer conversations, three advantages come up repeatedly:
A global healthcare organization recently replaced a fragmented SSE setup with Cisco Secure Access. Policy count dropped from700+to just74, and more importantly, they closed gaps where SaaS traffic was being inconsistently inspected, putting patient data at risk.
Now, their policies follow the user across every app and connection type, cutting risk and operational overhead in the process.
Security teams are protecting more than ever: remote work, hybrid data flows, IoT and OT devices, and AI-driven agents. Each adds complexity, and complexity is the enemy of effective security.
Unification isn't just a nice-to-have; it's how you maintain consistent protection without burning out your team. When every control shares the same context, enforcement is smarter, faster, and more reliable.
Cisco Secure Access deliverstheunified SSE platform enterprises need right now, simplifying policy management, strengthening security, and improving user experience. It's not just about replacing point tools. It's about replacing the point tool mindset with something stronger, faster, and built for the way work happens today.
See how Cisco Secure Access can unify your SSE fabric and make policy follow the user everywhere they go.
We'd love to hear what you think! Ask a question and stay connected with Cisco Security on social media.
Cisco Security Social Media
LinkedIn
Facebook
Instagram
X
 Hot Tags :
data center security
Cloud onRamp
cloud edge
cloud access security broker (CASB)
Cloud Managed Security
Cloud-Delivered Security
Cloud Identity
Cloud Security Analytics
Cloud Access
Hot Tags :
data center security
Cloud onRamp
cloud edge
cloud access security broker (CASB)
Cloud Managed Security
Cloud-Delivered Security
Cloud Identity
Cloud Security Analytics
Cloud Access